The Hunt for “Vulnerability Inbox 0”
Emerging Techniques to Reduce Application Vulnerability Overload
Speaking with several CISO and security leaders over the last few months, it is clear that Vulnerability Management remains a significant challenge for many organizations. Security teams often find themselves overwhelmed by the sheer number of vulnerabilities detected, struggling to categorize, prioritize and address them effectively. On average, 100,000 vulnerabilities remain unaddressed in an organization’s security backlog. With developers leaning more and more into AI-powered code development tools like Github Copilot, which rely on human trained data, vulnerabilities will likely continue to rise. Indeed, a study at NYU had revealed that 40% of code produced by Copilot was indeed vulnerable, while a study at Stanford showed developers believed their code was more sound when using an AI tool when the code was actually more vulnerable.
With the emergence of SCA (software composition analysis), we have vastly increased the amount of vulnerabilities we detect, but that has left us with a different problem: How do we fix them when there are so many? The reality is that while we have a relatively firm grasp of detection with tools such as Snyk, Contrast Security, and Checkmarx, we have not yet solved the human problem associated with remediation. The issue with remediation falls into 2 categories:
Focus and Prioritization: Using the limited developer time available to focus on what vulnerabilities need to be addressed more urgently
Automating Developer & Security work: It's hard to get valuable developer time spent on security issues over product features
In order to address this, a new crop of companies have started to develop over the last few years. In the following, I wanted to highlight some of the really interesting approaches and techniques that are being developed to usher in the next era of application vulnerability management.
Pre-Production Reachability
In the face of overwhelming vulnerabilities within an application, it's essential to discern their actual impact. Many of these vulnerabilities may reside in third-party code that isn't even executed by the app, rendering them non-exploitable. This raises an important consideration: are some vulnerabilities essentially unreachable and, therefore, less critical to address immediately? By identifying these unreachable vulnerabilities, developers and security teams can prioritize their efforts on those vulnerabilities that genuinely affect the application in its current production state. This approach is called Reachability Analysis. Although eventually, in a perfect world all vulnerabilities warrant attention, understanding where to begin can significantly streamline the remediation process and limit the precious impact to developers.
Reachability-based SCA by Endor Labs
One example of startups trying to address this is Endor Labs. Endor Labs' approach to SCA reachability is centered around the concept of analyzing the code behavior at build time to identify reachable vulnerabilities at the function level. This is achieved through a combination of static analysis of source code, manifest files, file system, and package manager data. Static call graphs are used as a precise instrument for this analysis, enabling the identification of direct and transitive dependencies, including those not declared in manifest files. This approach not only helps in prioritizing reachable risks but also provides a comprehensive view of all dependencies in use, improving the accuracy and reducing the time and cost associated with remediation. Endor Labs' method is distinguished by its ability to map vulnerabilities in open-source libraries in their real-world context, leveraging call graphs to trace relationships between software functions. This enables a more precise identification of vulnerabilities that are actually exploitable in the application's unique context.
The end result of this is self-evident. By using reachability as a core tenant to understanding priority of remediation of a particular vulnerability, security teams can be more targeted in trying to prioritize fixes within their control. Solutions like Slim.ai can then also provide a shared workspace among customers and software vendors to coordinate vulnerability fixes involving third parties.
Runtime Instrumentation for Vulnerability Prioritization
Runtime Instrumentation, when used in the context of vulnerability prioritization, embeds monitoring capabilities directly into the application code, thus actively observing its interactions with various components like libraries and infrastructure. This method is particularly advantageous for identifying and prioritizing security vulnerabilities in real-time. By monitoring internal operations, runtime instrumentation can detect unusual patterns or behaviors that may indicate security flaws. This immediate detection allows for quicker response to potential threats, reducing the window of opportunity for exploitation.
The detailed insights provided by runtime instrumentation into the application's functioning enable a more nuanced assessment of vulnerabilities. It helps in understanding the context and potential impact of a security flaw within the application's unique environment. This context-specific information is crucial for prioritizing vulnerabilities effectively, ensuring that the most critical issues are addressed first.
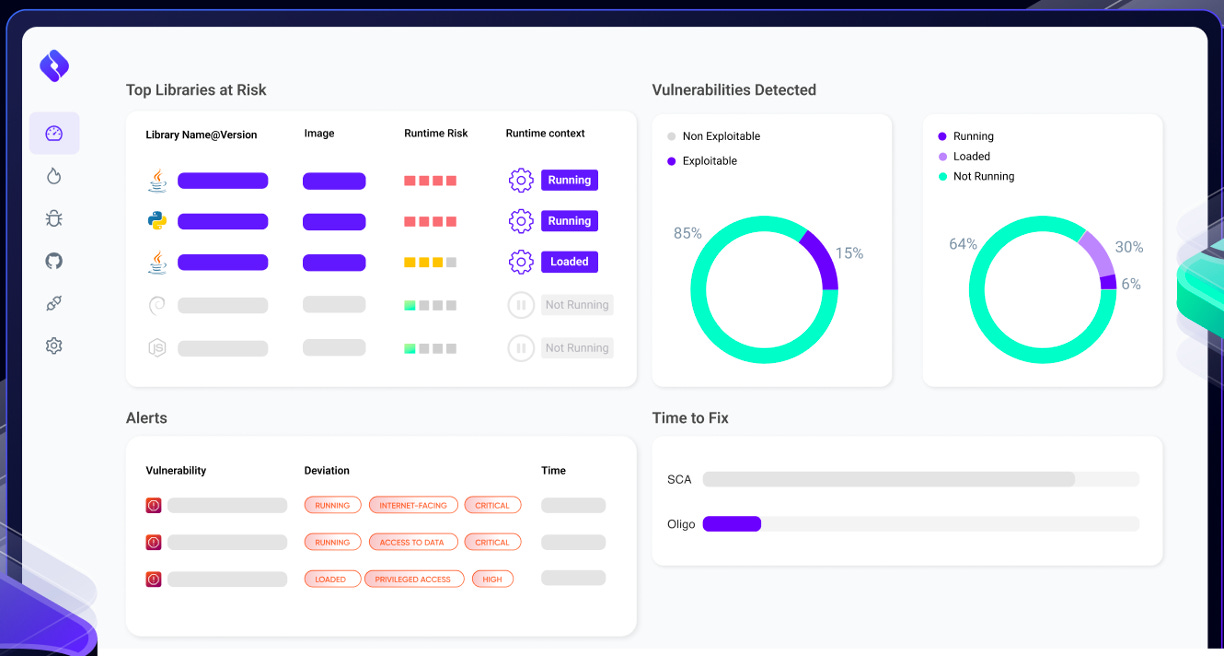
One company in the space is called Oligo Security. The company’s product utilizes dynamic library-level analysis and behavior monitoring to identify vulnerabilities in real-time. This approach is particularly effective in detecting vulnerabilities in open-source libraries during runtime. By analyzing each library's behavior, Oligo creates profiles of legitimate activity and generates alerts or blocks suspicious deviations from these patterns. This targeted approach filters out about 85% of alert noise, significantly reducing cybersecurity fatigue.
Oligo Runtime-Based Vulnerability Prioritization
Oligo's platform is based on the eBPF subsystem, a technology developed for the Linux kernel. This allows Oligo to run efficiently without compromising on performance or stability. The platform's focus is on identifying vulnerabilities based on the context of the running application, thereby helping developers and security teams focus on the actual attack surface, which is often a fraction of the vulnerabilities identified by traditional tools. This method not only streamlines the security process but also accelerates development by allowing teams to concentrate on the most relevant issues.
Autonomous Product Security Engineering
Autonomous product security engineering represents a significant advancement in the realm of application security. By integrating directly into developers' workflows, this approach can effectively alleviate vulnerabilities in real-time. It operates by analyzing code during the development process and proactively suggesting code fixes. This method not only identifies potential security issues but also offers immediate, actionable solutions, seamlessly blending security practices with the development process. This integration helps maintain the flow of development while ensuring that security is a continuous, integral part of the process rather than an afterthought. Such a system significantly reduces the time and resources typically needed for vulnerability detection and remediation, and it enhances overall application security without disrupting the development cycle.
Pixeebot monitors code repositories and provides high quality fixes instantly
Pixee.ai has pioneered a developer tool for enhancing application security. Their product, Pixeebot, is designed to identify and fix vulnerabilities within code, effectively streamlining the software development process. By integrating directly into the development environment, Pixeebot offers high-quality, instant fixes as developers or AI-assistants work on code. This approach ensures that developers can maintain their productivity and focus while simultaneously enhancing the security and quality of their code. Essentially, Pixeebot acts like an automated security engineer, seamlessly integrating into the development workflow and significantly reducing the backlog of security tickets by transforming code scan results into actionable pull requests for merging.
Conclusion
The emerging techniques in application vulnerability management, such as Pre Production Reachability, Runtime Instrumentation, and Autonomous Product Security Engineering are clearly attempting to solve one of the biggest problems in cybersecurity in vulnerability overload among security teams. As many breaches still begin with unpatched vulnerabilities, it is still a key obstacle in getting a strong security posture among enterprises. By prioritizing actionable vulnerabilities, integrating directly into developers' workflows, and employing advanced technologies, these approaches are not only addressing the current challenges in vulnerability management but also paving the way for more efficient and secure software development practices.
Special thank you to Sean Cassidy, Mike Schwartz, Arshan Dabirsiaghi, Ed Bellis and Surag Patel who provided incredibly valuable input and helped me think through some of these concepts.