Not long ago, I wrote about a new wave of Programmable Defense platforms, and how they fit within the broader evolution of cybersecurity. At the time, it felt like a logical progression: We’d seen the slow but steady rise in both sophistication and volume of attacks—and the corresponding call for more adaptive, security engineering-friendly security products. Now, with the advent of LLMs, that progression has taken a major leap forward and is driving cybersecurity into a new era: the Autonomous Defense.
The Autonomous Defense is a collaborative paradigm in cybersecurity where human creativity and AI work together to detect, contextualize, and respond to threats across entire kill chains in real time. It represents the evolution from rigid, static black-box security solutions to adaptive, programmable systems that seamlessly integrate human oversight with AI-driven automation.
The need for Autonomous Defense is a response to more than just an accelerating volume of attacks; it’s also addressing threat actors’ evolution in style, creativity, and deception.
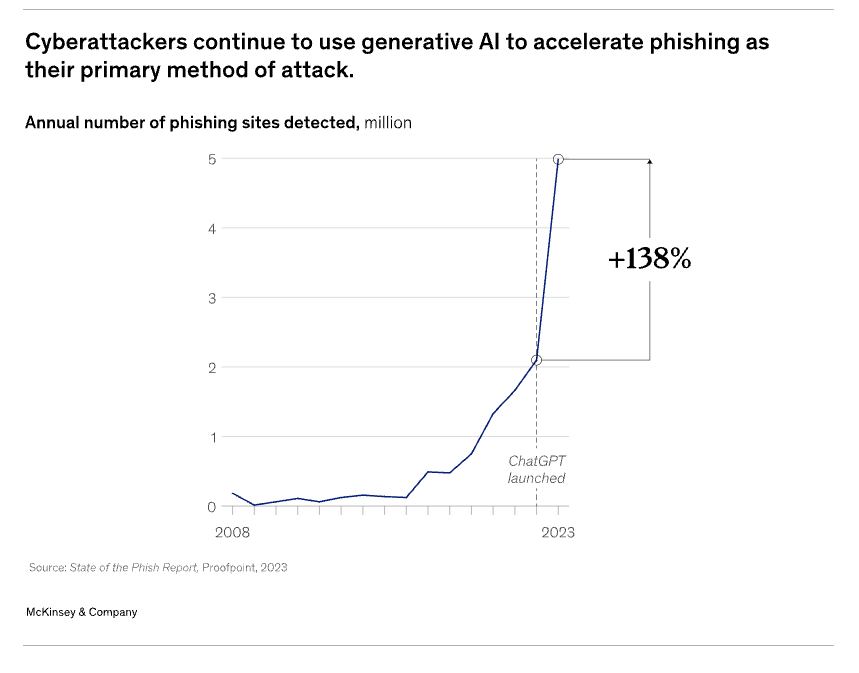
McKinsey’s data on phishing alone highlights the surge in AI-enabled exploits: more intricate social engineering, more convincing synthetics (think deepfake audio and video), and a flood of new email tactics that bypass traditional filters. In one well-known example, threat actors leveraged deepfakes to pose as a company’s chief financial officer and convinced a finance worker to pay out $25M.
And let’s be clear: It’s not just the malicious side harnessing these AI engines. Security teams are actively embedding AI into their workflows—raising the bar for rapid detection, real-time contextualization, and automated responses.
What does all of this mean? If you talk to the folks who came up through the ranks of BlackHat and DEFCON, you’ll see a common theme: security professionals are done waiting for vendors to patch together stale, rigid solutions. They’re demanding tools that can adapt as fast as the threats do–and do so in a way that maximizes both security outcomes and operational efficiency. The Autonomous Defense is responding to that call, empowering teams to reduce the cost and time of defending against increasingly sophisticated attacks, while freeing up human defenders to focus on the highest-value challenges.
Let’s break down the foundational elements of the Autonomous Defense and how they coalesce into this new paradigm:
Programmable: Where AI and Humans Collaborate
Programmable security has long been part of our thesis at Decibel. It represents the critical fusion of flexible toolsets that can adapt as attacks evolve—and, more importantly, do so seamlessly with human oversight. A big part of making that happen lies in how systems, humans, and AI “talk” to each other.
A lot of security products historically hid behind black-box algorithms. If it flagged something, good luck debugging the “why.” Now, we’re seeing a shift to detection tools that expose a domain-specific language (DSL). Think of Sublime Security’s approach, where everything from rule creation to threat hunting can be expressed in a clear, programmable format. It’s a shared language between you and your AI, reducing confusion and “hallucinations” that can happen when an AI tries to guess your intent without a well-defined structure.
This synergy is the same reason code-generation platforms like Cursor and Codeium have been so effective: humans design the logic and context, AI executes the heavy lifting. The result is faster, more accurate rule-writing and detection logic that can be tuned on the fly. We often forget that many cyber risks hinge on “time to detection.” If your detection rules can be automatically refined and iterated within minutes—not weeks—you effectively take away one of the biggest advantages attackers have.
Contextualization: Enriching without reducing signal
Silos are an unfortunate byproduct of the rapid technology sprawl in security. We have specialized tools for threat intelligence, incident response, vulnerability management, threat hunting, endpoint monitoring—the list goes on. But the reality is that kill chains don’t respect product boundaries. AI-driven attacks can pivot quickly from a phishing exploit to privilege escalation on your network, and from there, to data exfiltration in your cloud environment.
To truly defend in real time, we need a holistic vantage point. That’s where contextualization comes in. Imagine if your vulnerability management system and threat intelligence feeds were fully merged. Instead of receiving an alert saying, “Remote code execution vulnerability in product X,” you’d also get context: “APT Group Y has been exploiting this exact vulnerability in the last week, targeting financial institutions similar to yours.”
Now you don’t just know there’s a problem—you understand the likelihood and potential impact. You prioritize a patch. You escalate within your team, because you see the real risk of lateral movement in your environment. It’s basically the difference between an alert and a narrative. And that narrative is what teams need to respond swiftly and effectively.
One big step in that direction is the collapse of multiple security categories into a single, integrated chain. If threat intel informs vulnerability management, which directly ties to patching or exploit-blocking, that reduces both manual handoffs and the risk of something slipping through the cracks. AI models trained on your specific environment can automatically flag the vulnerabilities most likely to be exploited in real time, driving meaningful risk-based prioritization rather than generic best practices.
For instance, Empirical Security is leveraging OSINT and attack telemetry, mining its own proprietary data models and EPSS to build more advanced, localized models. Rather than depending on generic indicators, it aggregates and analyzes data from a worldwide network of sources to stay ahead of emerging threats. This shifts the approach of security teams from a reactive to a predictive and preventive mindset. By combining EPSS-based predictions with their contextual threat analysis engine, it can identify high-probability weaknesses specific to an organization’s profile, industry, and infrastructure. This holistic, intelligence-driven approach transforms raw alerts into actionable narratives, helping security teams not only detect issues faster but also understand the “why” and “how” of each threat—empowering them to prioritize and remediate with far greater precision.
Digital Twins: Real-Time Threat and Defense Simulations
We all know the classic tabletop exercises and third-party pen tests that happen every quarter (or year, if you’re unlucky). They’re valuable, but also resource-intensive and slow. You’re basically simulating known attacks, capturing the results, then hoping to find and fix the gaps before the adversaries do.
Enter digital twins (DTs). Already commonly used in industries like aerospace and manufacturing, digital twins help organizations model complex systems like jet engines or assembly lines, enabling them to simulate performance, predict failures, and optimize operations in real time by testing changes in a virtual environment before implementing them in the real world. In the context of cybersecurity, a digital twin is a virtual model of your organization’s infrastructure—networks, applications, endpoints, and even the workflows your security teams use. By simulating attacks in this environment, you can stress-test new defensive strategies without risking actual systems.
Digital Twins can point out the transformative potential for defenders. Researchers describe how Cyber Digital Twins (CDTs) focus specifically on cybersecurity functions, letting security teams simulate attacks, evaluate patch effectiveness, and predict the downstream impacts of compromises—all without real-world disruption. They’re like living blueprints that track real-time changes, enabling you to validate configurations, hunt for zero-days, and quickly pivot to new defensive measures before the threat actors can adapt.
To me, digital twins represent the next logical step in cybersecurity resilience. Because once you can replicate your entire security environment in code, you can unleash AI to run hundreds—maybe thousands—of “what if” scenarios in parallel. This advanced simulation closes the gap between detection, analysis, and remediation.
AI-Powered Workflows: Driving Down Toil
Even in 2025, so much of cybersecurity still involves repetitive, manual tasks. Security teams are inundated with alerts, logs, tickets—some of which are critical, many of which are false positives or routine. This grind leads to fatigue, burnout, and inevitably, missed signals.
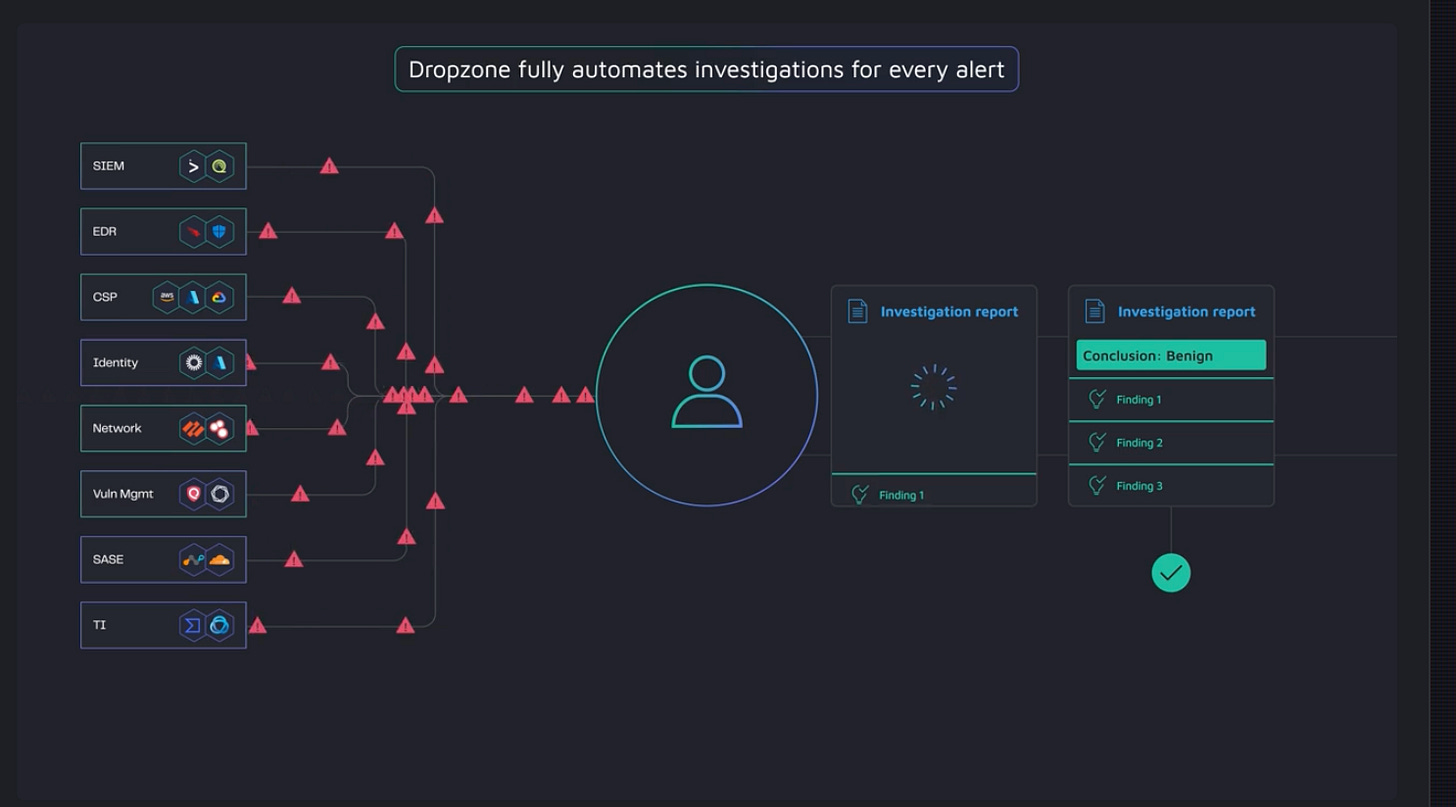
Automation is nothing new, but the level of workflow optimization we can now achieve with AI is next-level. Products like Dropzone reduce toil by automatically categorizing and responding to routine alerts, letting defenders focus on the nuanced tasks that require human judgment. That’s where we want the human defenders—applying their experience, creativity, and gut instinct to tricky edge cases, advanced threat hunting, or major incidents that need strategic input.
There’s a virtuous cycle at play: The more tasks you offload to a well-tuned AI system, the more time you free up for the human side of the collaboration. Your team can invest energy in improving detection logic or analyzing novel threats.
Conclusion
The Autonomous Defense is a convergence of principles that have been brewing for years: programmability for adaptive detection rule-making, contextualization that breaks down data silos, real-time simulation via digital twins, and AI-driven workflow optimization that frees up human defenders to to focus on high-impact work while lowering operational costs and improving the ROI on security.
Not every “autonomous defense” product of the future needs to include every single feature in this list. But these concepts—programmable security, integrated intel, digital twins, and streamlined workflows—serve as a guidepost for what’s possible right now. AI has changed the game for attackers, but it’s also leveling up our defenses in ways we couldn’t have imagined a decade ago.
If you’re building (or dreaming of building) something that fits these principles, I’d love to hear from you. Because I believe they provide a compelling path forward to embrace this era of collaborative AI-human defense—and help shape the tools that define it.
In many ways, the folks who cut their teeth at BlackHat and DEFCON did us a favor by demanding more flexible, programmable solutions. Now that they’re in leadership roles, it’s time for us to answer the call and deliver.
Big thank you to Josh Devon (Flashpoint), Damien Lewke (Arctic Wolf) and Ed Bellis (Kenna Security) for providing massively insightful feedback on this piece and helping me refine my thoughts on this topic.